Welcome to a comprehensive guide on Evil Twin Wi-Fi Attacks. If you're curious about how attackers replicate legitimate wireless networks to intercept sensitive data, you're about to enter a scenario where things aren't quite what they seem.
We'll begin by explaining the concept of an Evil Twin attack, looking at its use in both ethical hacking and malicious activities. Next, we'll guide you through setting up a lab environment, which involves specific hardware and configurations.
In the practical section, we'll demonstrate a basic Evil Twin Wi-Fi attack using Airgeddon, a tool that streamlines this complex process. These step-by-step instructions will help you understand the technical details involved.
WHAT IS AN EVIL TWIN?
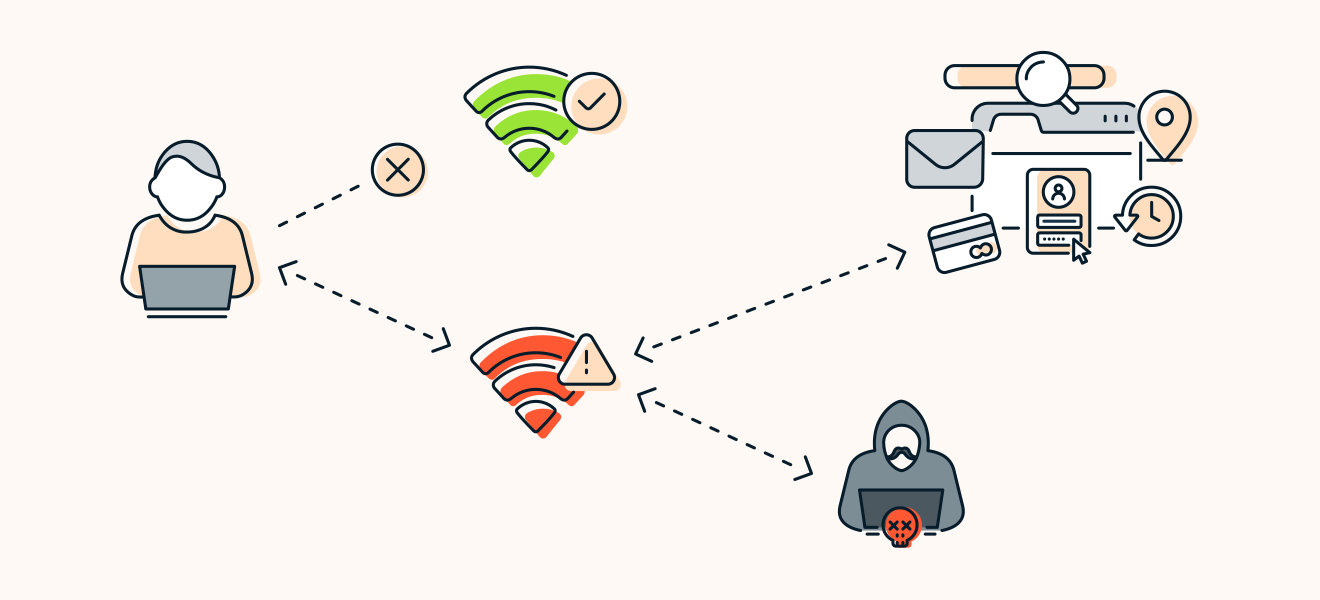
Picture yourself relaxing at your favorite coffee shop, enjoying a latte while using their complimentary Wi-Fi. What you may not realize is that the network you've connected to isn't the authentic coffee shop Wi-Fi, but a nearly identical setup by a malicious actor. This is known as an Evil Twin.
Evil Twin attacks commonly occur in public areas with free Wi-Fi, where users often don't verify the legitimacy of the network they're joining, making them easy targets for attackers.
An Evil Twin is a fraudulent Wi-Fi access point (AP) that mimics a legitimate network. It usually has the same name (SSID) and may even share the same MAC address, creating a convincing facade. This type of attack can be leveraged for both malicious and ethical purposes.
Malicious hackers use Evil Twin access points to intercept sensitive information from unwary users. Once connected, victims unknowingly provide attackers with access to crucial data like login credentials and financial information.
On the flip side, ethical hackers simulate Evil Twin attacks to enhance an organization's security. By performing these controlled attacks, they can detect vulnerabilities within a network and resolve them before they are exploited by malicious actors.
DISCLAIMER
It's important to emphasize this point; even if it seem harmless to scan your neighbor's Wi-Fi network, a website's server or any other network, do not attempt it without explicit permission. Engaging in hacking or penetration testing without authorization from the network owner is illegal.
Regardless of intent, performing scans or hijacking without permission can lead to serious legal consequences, including potential jail time, depending on your location. Relevant laws include:
- Computer Fraud and Abuse Act (United States)
- Sections 184, 342.1, 380, and 430 of the Criminal Code (Canada)
- Computer Misue Act 1990 (United Kingdom)
- Sections 202a and 202b of the German Criminal Code (Germany)
- Information Technology Act, Sections 43 and 66 (India)
- The Act on the Prohibition of Unauthorised Computer Access (Japan)
Always ensure you have proper authorization before conducting any hacking or penetration testing activites.
BEFORE WE START
To get the best out of this guide and successfully carry out an Evil Twin attack, you'll need to have certain hardware ready and ensure your operating system is properly configured. While we'll be using Kali Linux for this tutorial, if you're using a different OS, just keep an eye on the prompts in Airgeddon- it will notify you if any required libraries aren't preinstalled and guide you through the installation process.
Essential Hardware
Working with wireless networks requires a Wi-Fi card with two key functionalities:
- Monitor mode, sometimes called promiscuous mode.
- Packet injection capability.
Unfortunately, most internal Wi-Fi cards don't support these features. An external adapter is needed instead. For this demonstration, we used ALFA AWUS036ACH Wi-Fi Adapter, alongside Kali Linux 2024.
Step-by-Step Guide Using Airgeddon
1. Launching Airgeddon
If you don't already have Airggedon installed on your Kali Linux machine, you can install it by running the following command in the terminal:

After installation, simply launch the tools by typing sudo ./airgeddon.sh
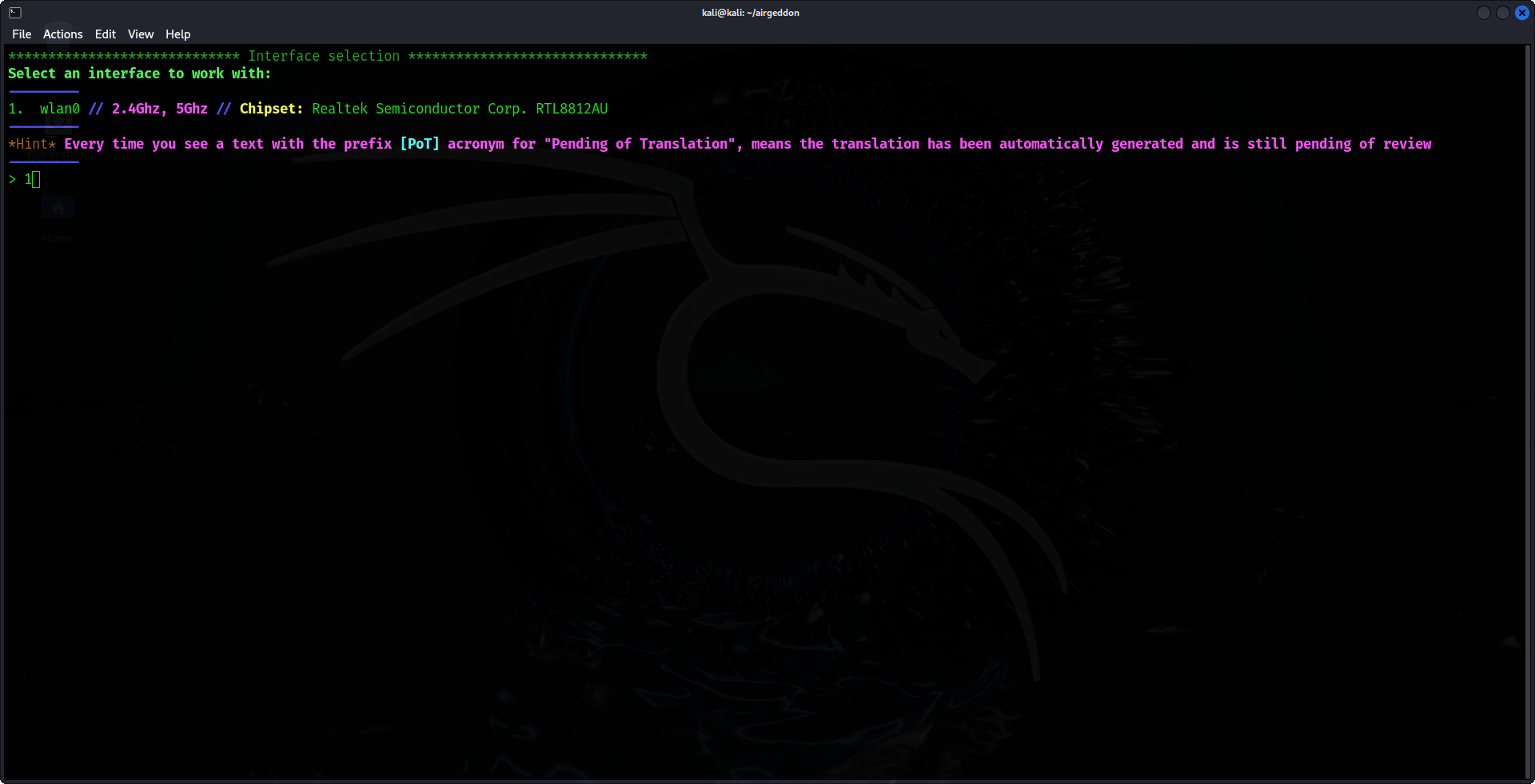
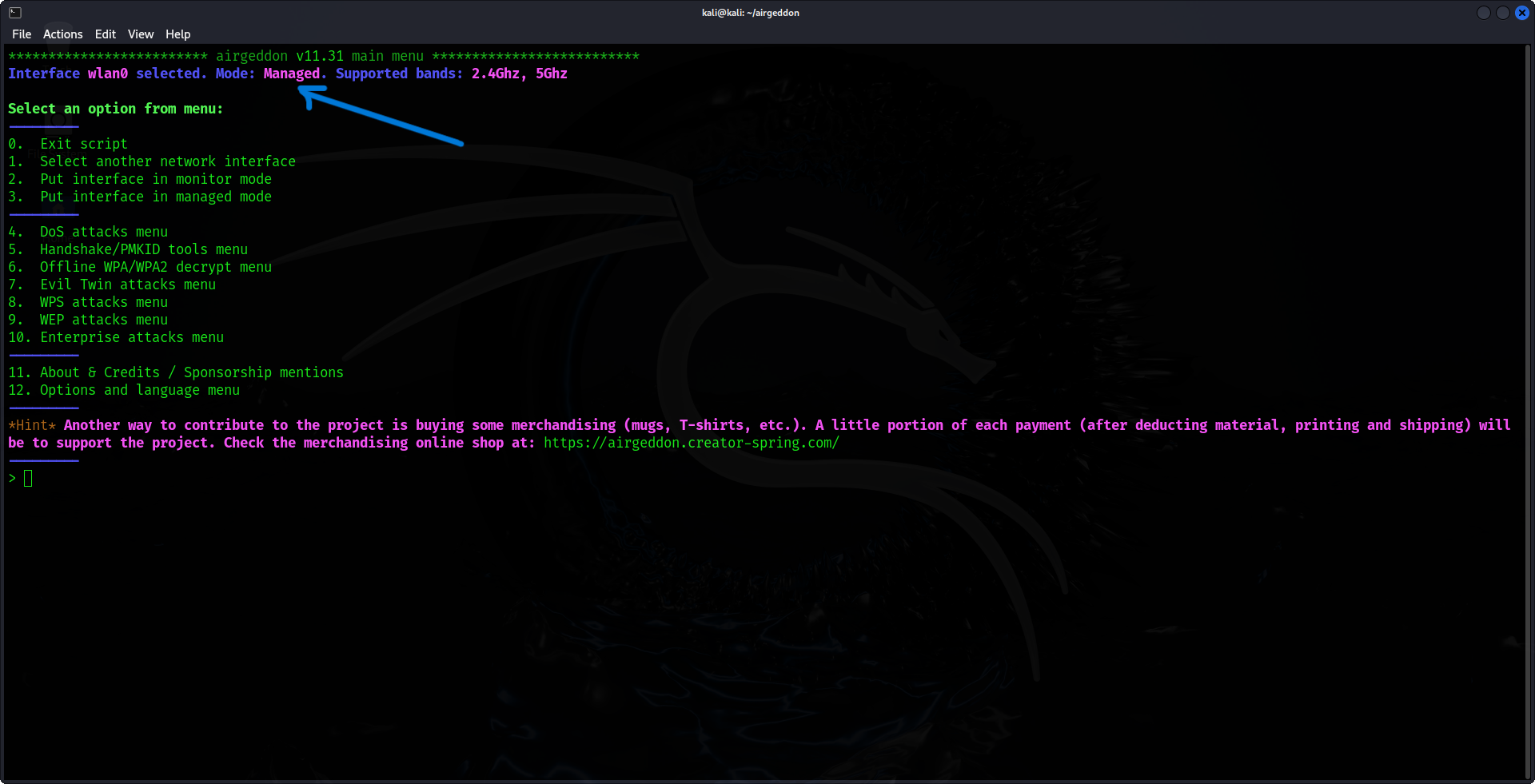
2. Select Your Network Interface
Once Airgeddon launches, it will prompt you to select a network interface. Your external Wi-Fi adapter should be listed. Simply type the number associated with your adapter and press ENTER to proceed.
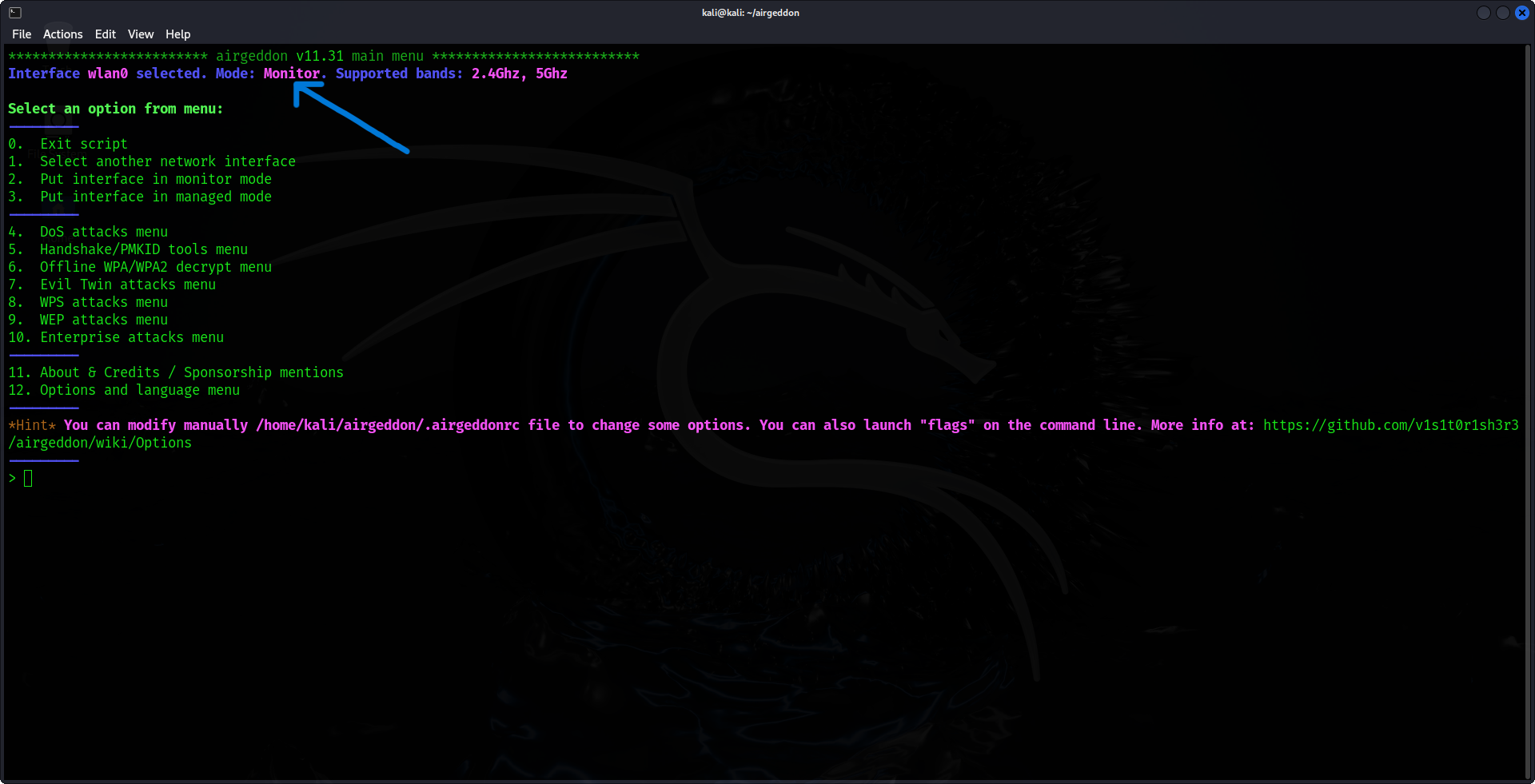
3. Enable Monitor Mode
Next, Airgeddon will prompt you to switch your selected network interface to monitor mode, which is essential for capturing Wi-Fi traffic. Choose the appropriate option to activate monitor mode for your interface.
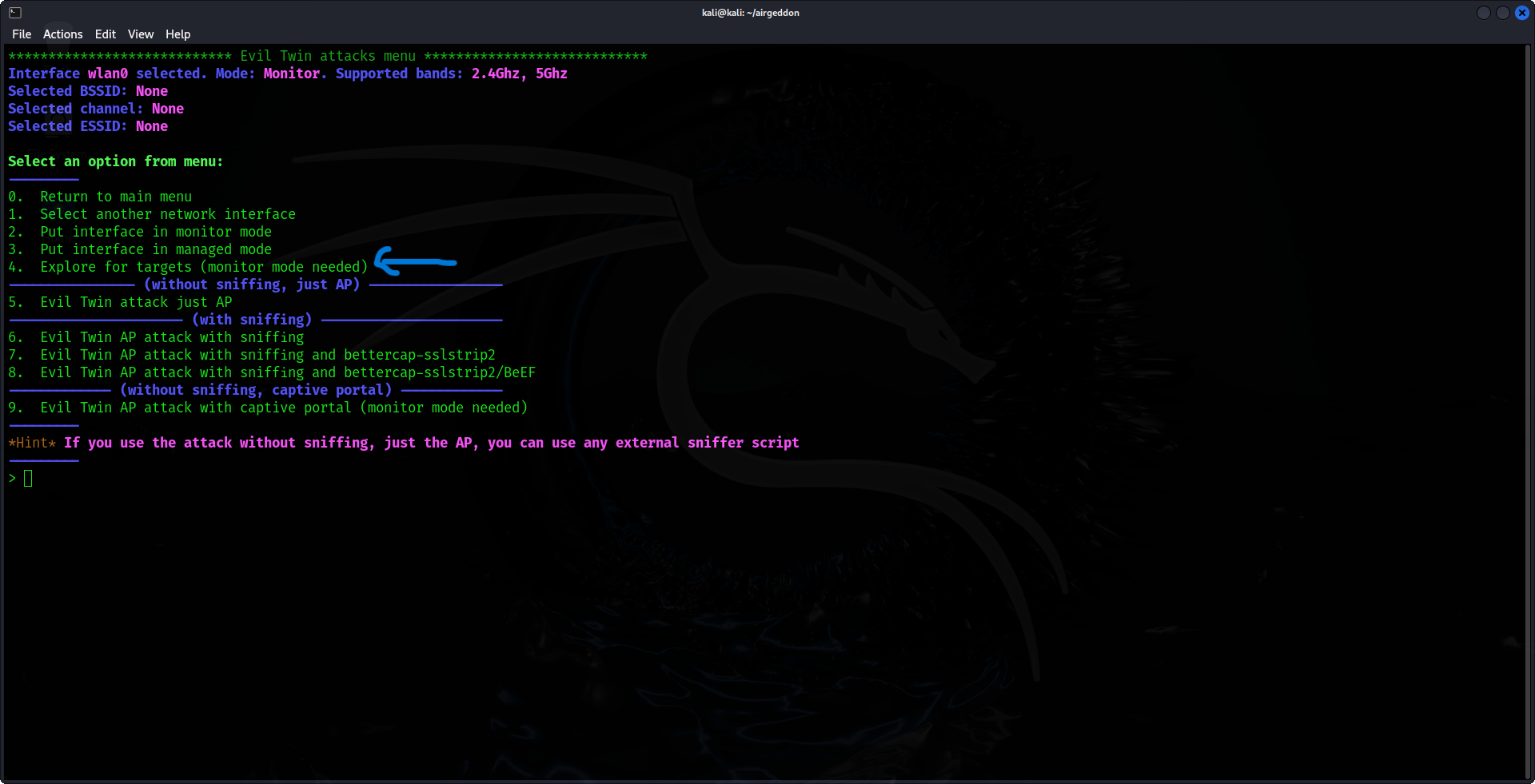
4. Choose the Target Network for the Attack
In the main menu, choose the option for an "Evil Twin AP attack." Airgeddon will begin scanning for nearby Wi-Fi networks. Once the list of networks is displayed, select your target by entering the number that corresponds to the network you want to attack.
5. Set Up the Evil Twin Access Point
Airgeddon will walk you through the process of configuring the Evil Twin Access Point (AP). It will automatically create a fake AP that mimics the target network, including the same SSID and MAC address. You'll be prompted to confirm or input certain details, but most of the setup is handled by Airggedon.
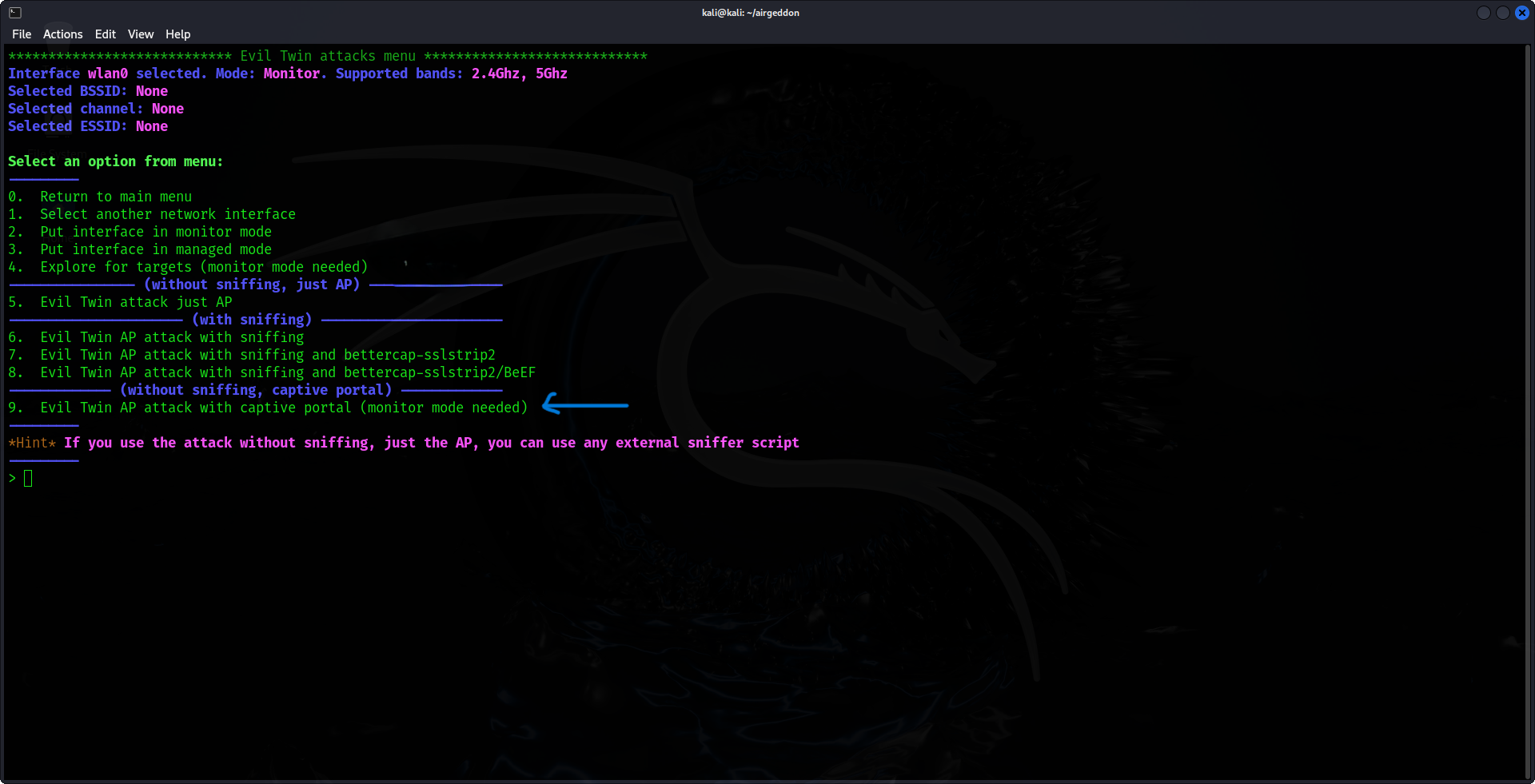
6. Execute the de-authentication Attack
Once the Evil Twin AP is configured, the next step is to compel the victim's device to disconnect from the genuine AP and connect to your Evil Twin. Airgeddon will automate this process by transmitting de-authentication packets, which will disrupt the victim's connection to the legitimate network.
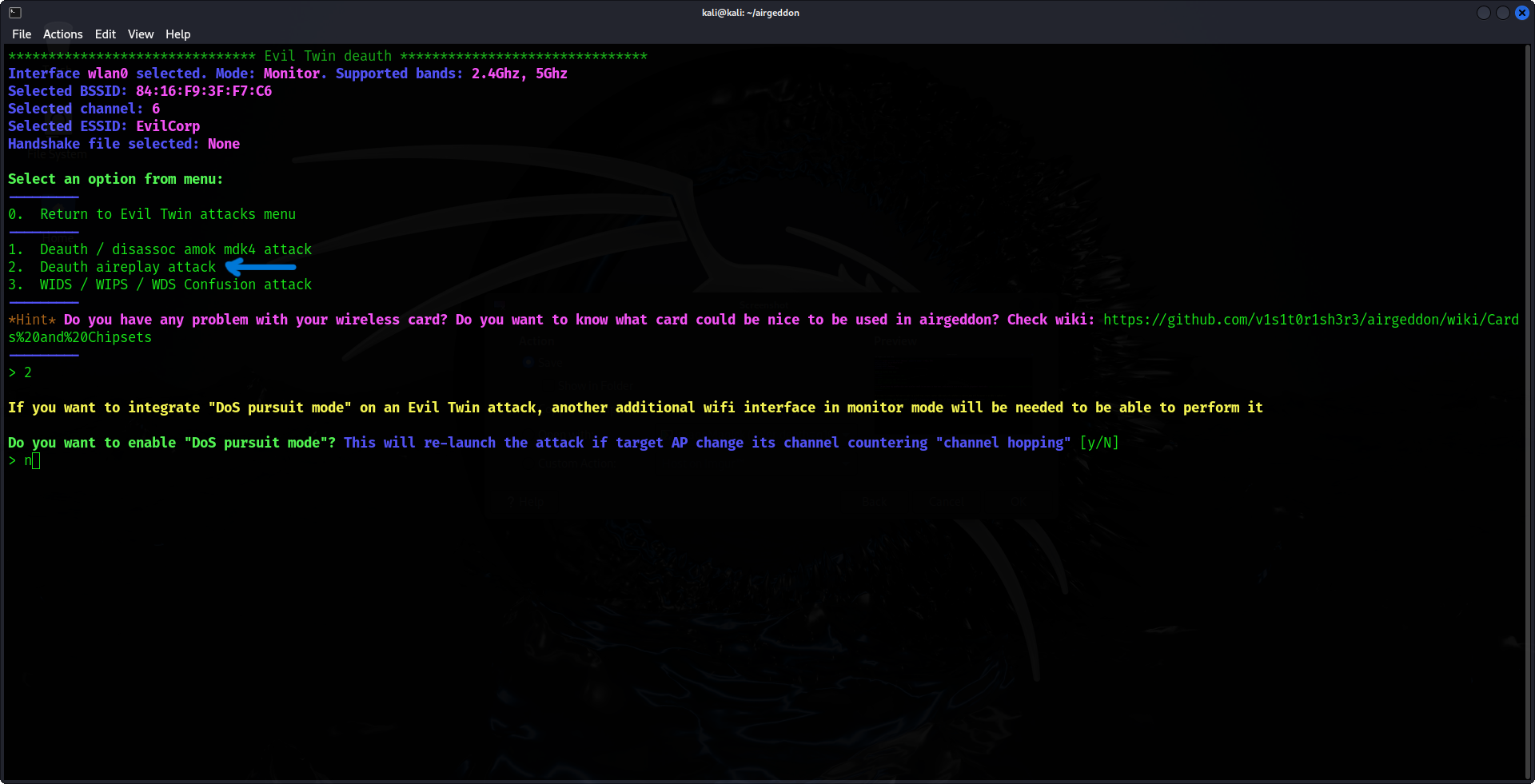
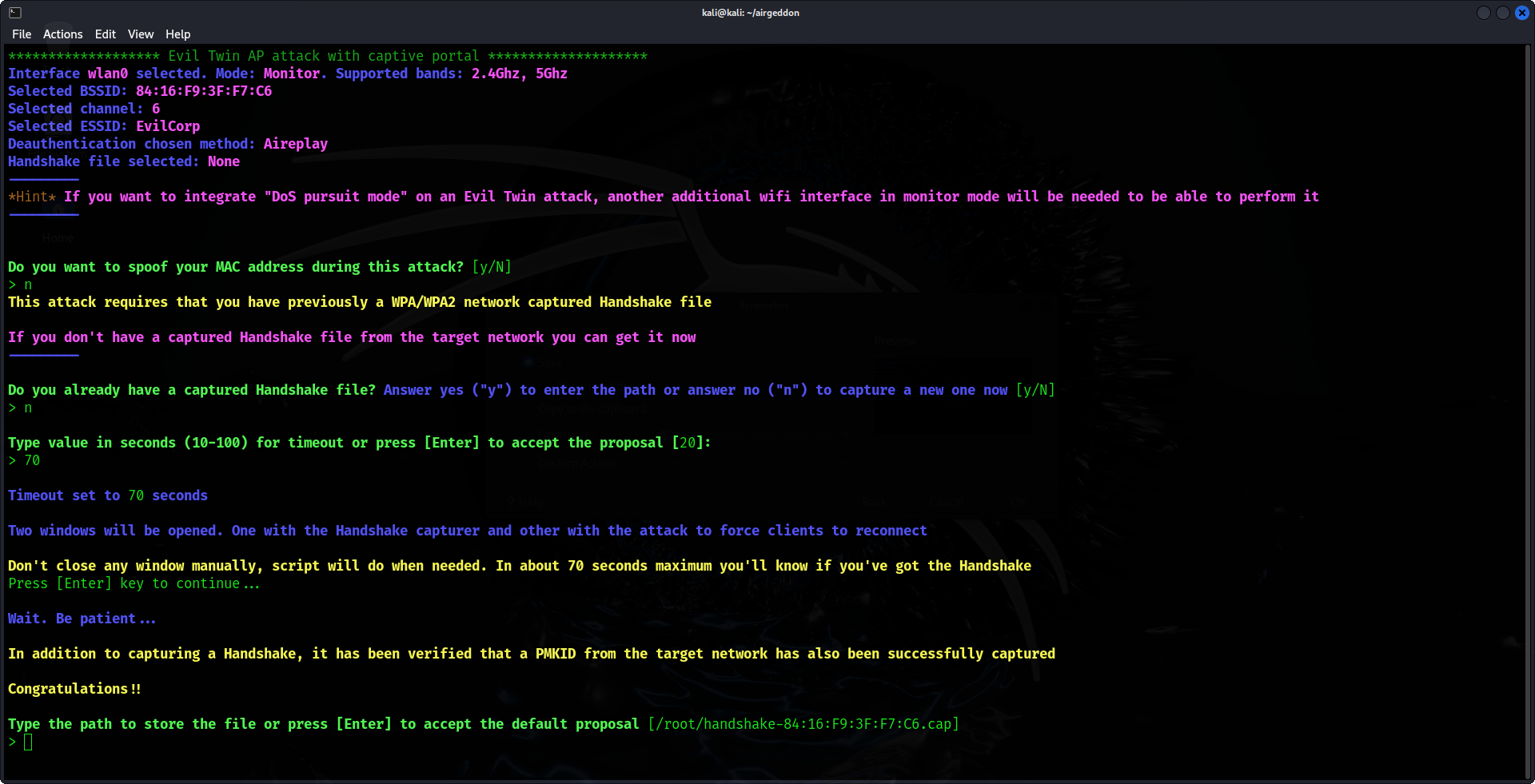
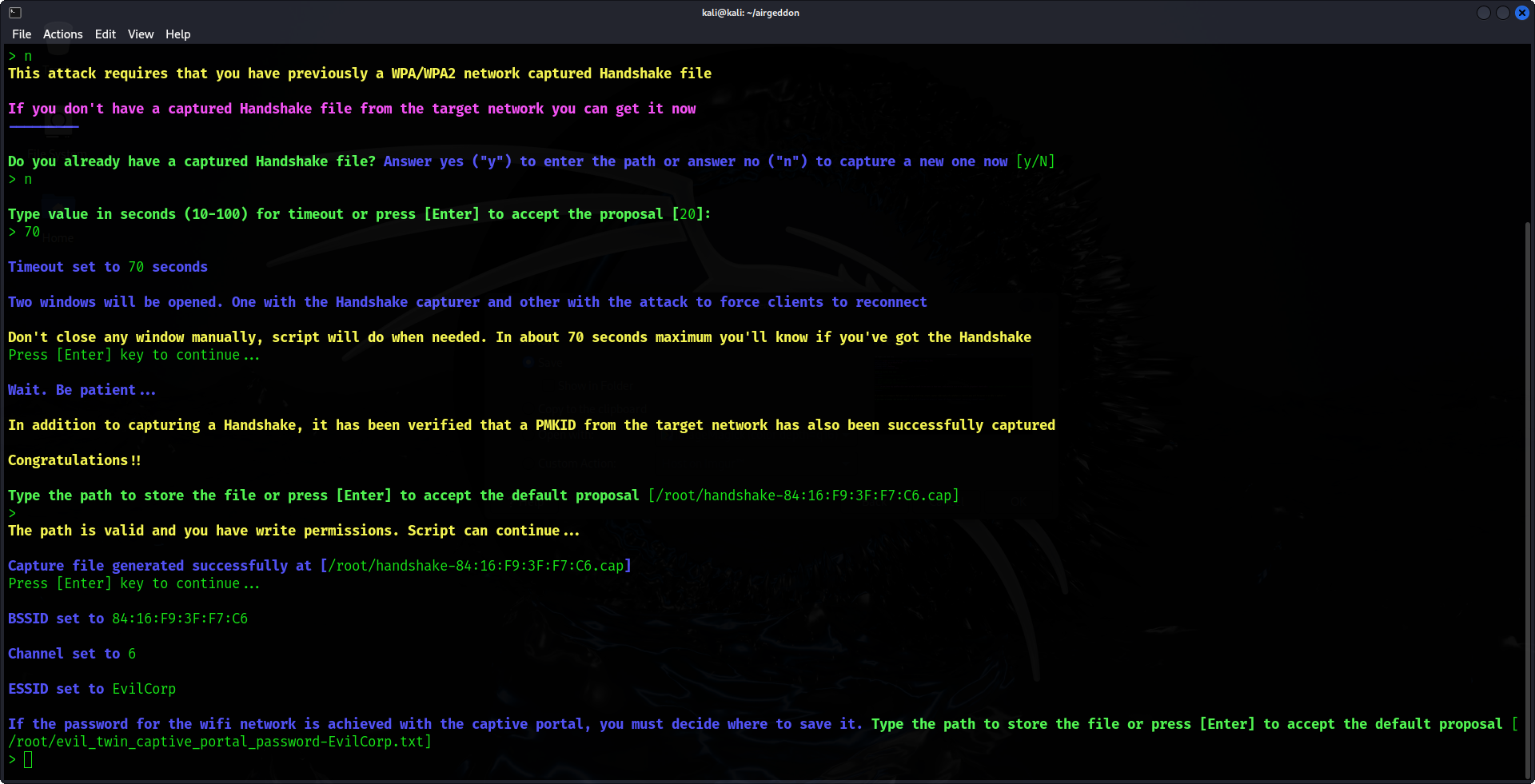
7. Configure the Fake Captive Portal
Following that, Airgeddon will create a counterfeit captive portal. This portal will prompt users who connect to the Evil Twin AP to provide a Wi-Fi password, claiming it is necessary for reauthentication.
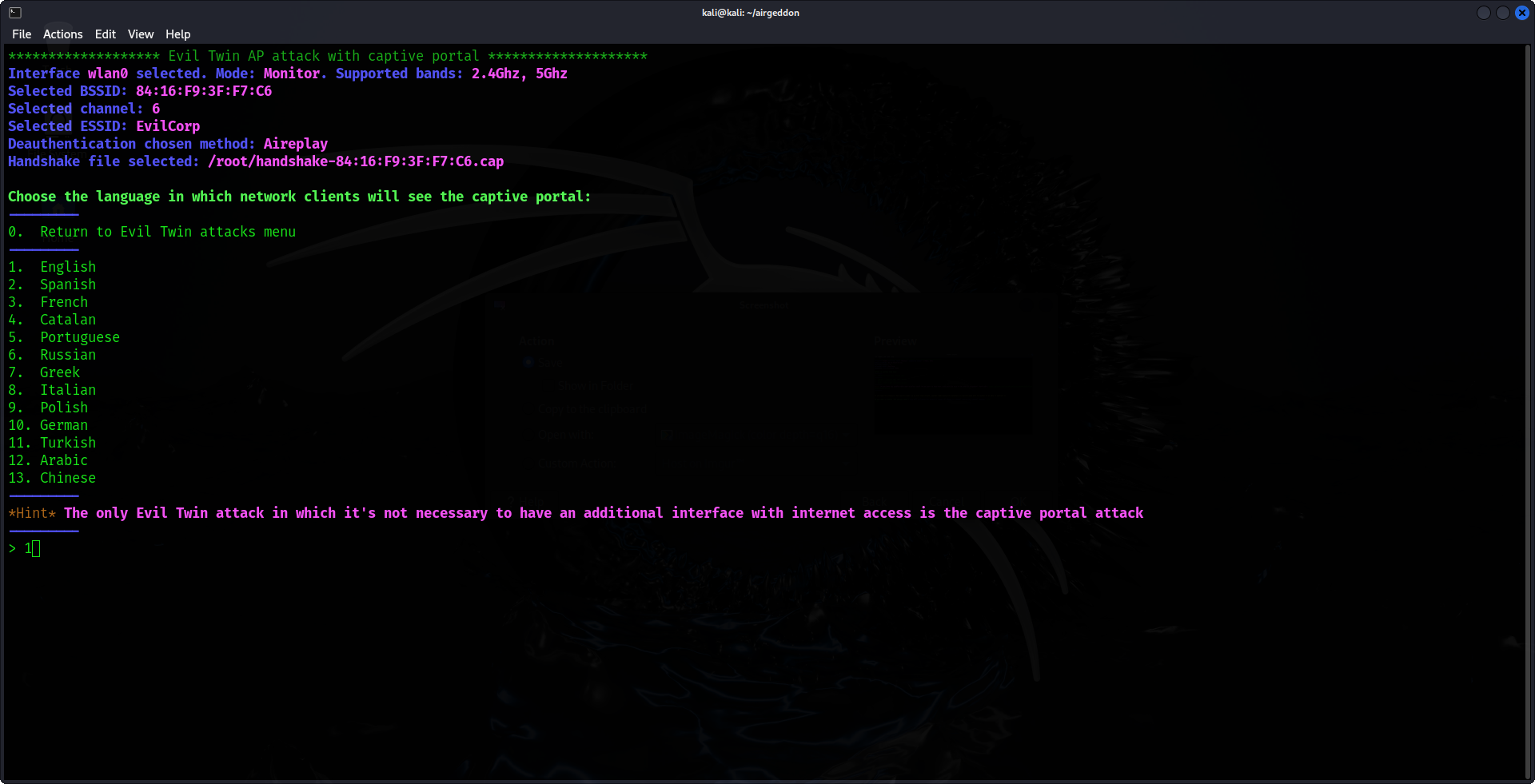
8. Capture User Credentials
Once a user submits their credentials through the captive portal, Airgeddon will record and display this information in your terminal.
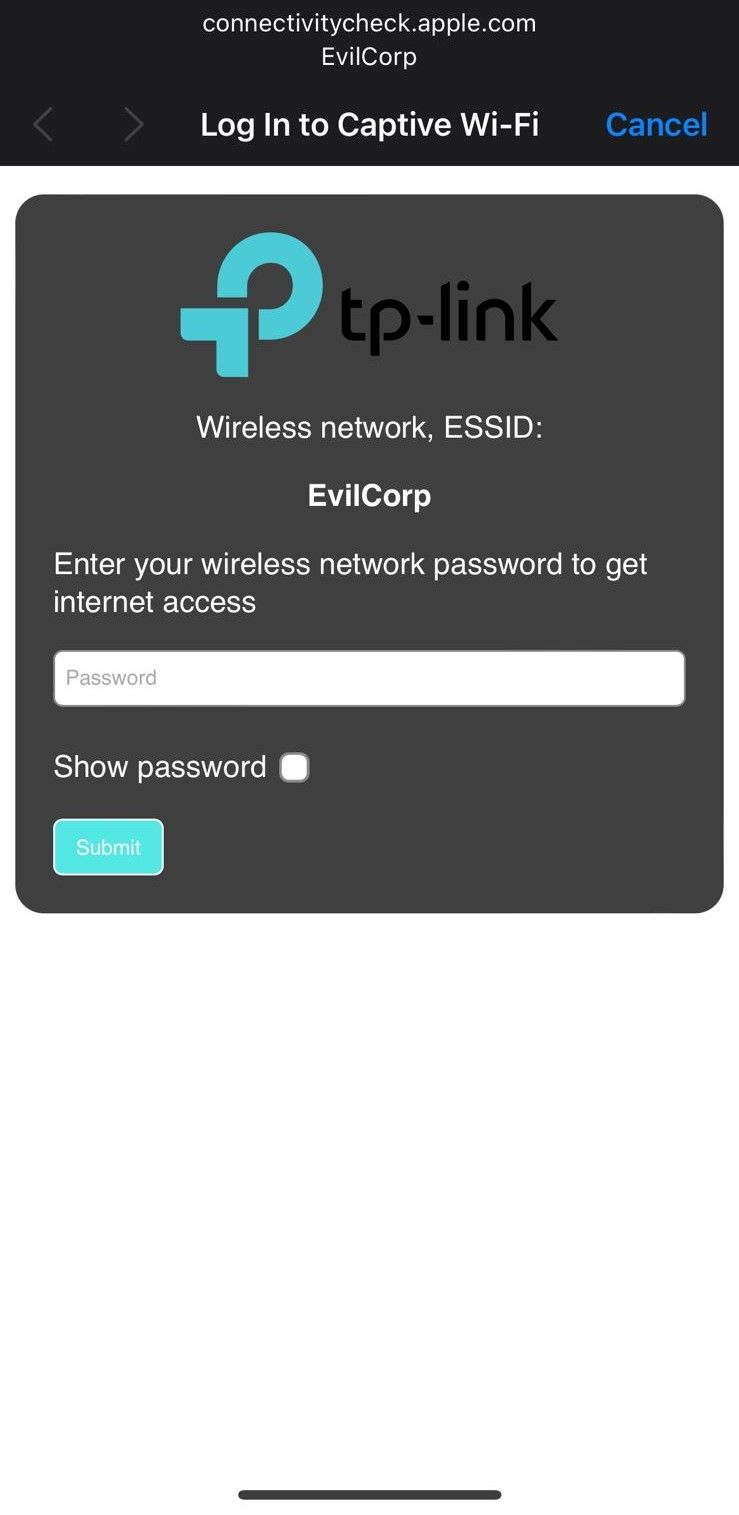
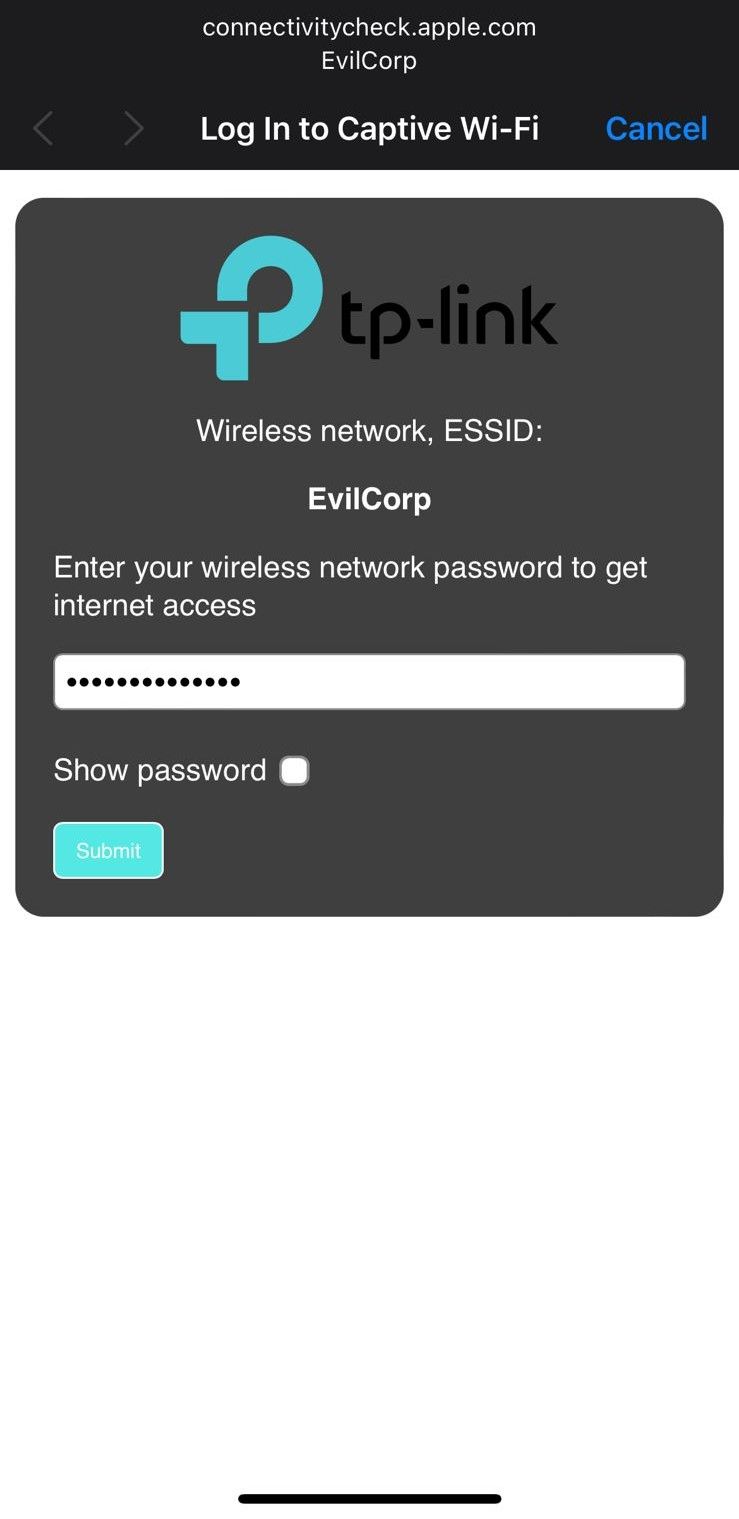
From the user's perspective, they will experience a de-authentication followed by an automatic reconnection to the Evil Twin AP. While a basic captive portal page is shown here, it's possible to implement a more sophisticated version.
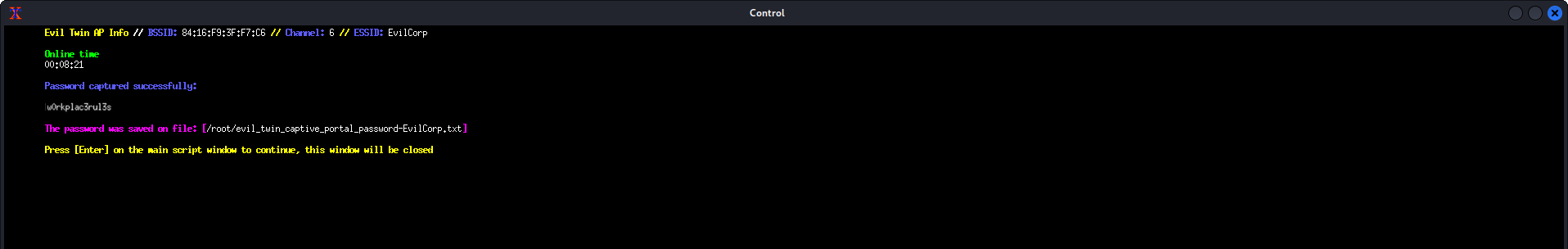
Once the user enters their password in the pop-up, the attack is complete and the credentials are stored.
CONCLUSION
In conclusion, we have traversed the intricate landscape of Evil Twin Wi-Fi attacks, starting from the foundational concepts to performing a basic operation, as well as delving into the complexities of more advanced techniques. Much like an expansive ocean, the realm of cybersecurity is constantly evolving and can sometimes seem daunting. However, keep in mind that every significant journey begins with a single step, and today, you have made a considerable advancement in enhancing your understanding.
Author: Harshad Pawar, Penetration Tester
LinkedIn: Harshad Pawar